-
 chevron_right
chevron_right
Movim 0.24 Mueller
Timothée Jaussoin · pubsub.movim.eu / Movim · Yesterday - 20:51 edit · 2 minutes · 6 visibility
Movim 0.24, codename Mueller is out. Let's dive in all the new exciting things that you can find in this new release!
What's new?
XEP-0386: Bind 2, XEP-0388: Extensible SASL Profile and XEP-0474: SASL SCRAM Downgrade Protection
Movim was definitely not the first one integrating those XMPP extensions but their implementation finally brings a much modern authentication stack to the project.
Bind 2 and Extensible SASL Profile greatly simplifies the authentication flow allowing Movim to connect (and reconnect) even faster, don't worry the older method is still there and will allow you to connect on #XMPP servers that don't support yet this new mechanism.
SASL SCRAM Downgrade Protection is a small security layer that sits on top of SASL (the authentication framework used by XMPP) to prevent channel-binding downgrades attack during the handshakes methods. It starts to be enforced by several servers nowadays such as ejabberd.
We would like to thank fabiang that did an awesome work on the #PHP #SASL library to add the SCRAM Downgrade Protection to it and allow a proper integration of the feature in Movim. Thanks!
Complete page navigation loading refactoring
You may not have seen it but a big #refactoring work was done under the hood to greatly simplify the navigation system in Movim.
This allows you to have a working and reliable "back-button" experience across the user interface. It is actually especially noticeable on mobile where the back button is used a lot to switch between the different UI elements (drawers, pages, sliders...).
This refactoring also fixed a few important bugs regarding the user interface internal events that were creating weird behaviors. For example, in some cases, when you were loading several time the same page in a row, the same event was attached several time to some buttons creating an mess when clicking on it.
And finally the browser - server connection (that relies on a Websocket) was also refactored and simplified fixing numerous connectivity bugs that we had until now.
Changes when publishing an article
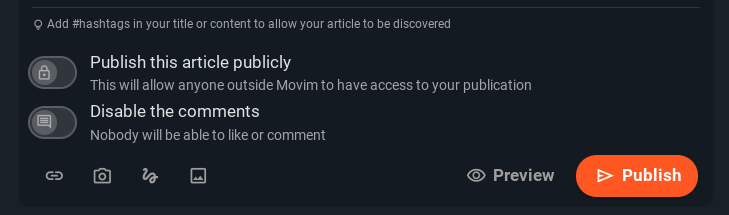
The post publication form was slightly reorganized. The post privacy toggle was more clearly defined and another one, to disable comments and like, was added next to it.
Interface improvements
Since its big rewrite in 2014 Movim always relied on the Google #Material Design system. This version continue the integration of Material 3 with the redesign of the search and chat boxes as well as small forms and buttons details.
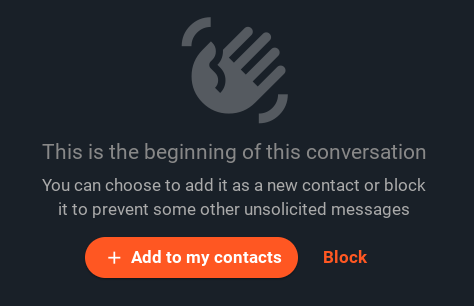
A new placeholder was also added when starting a new chat allowing you to quickly add the user to your contact list or block him.
Other fixes and improvements
A few #OMEMO bugs were also fixed, especially the bug #1261 that was preventing Movim users to decrypt their own messages in chatrooms.

We also fixed an annoying video-conferencing bug (#1274) that was preventing Movim to accept some specific audio and video calls. This allows Movim to process calls properly coming from #SIP bridges and to connect with SIP clients like Linphone !
We would like to especially thanks toastal for his several contributions to the project including internal image size picture management, a big refactoring of the internal language management system and some more minor interface and performances fixes.
What's next?
This version prepared the last important bricks required to introduce the early steps of the big audio and video-conferencing refactoring, especially with all the navigation and interface internal events management that was done the past few releases.
We will tell you more about it soon, stay tuned!
In the meantime, please share the good news around you and don't forget to update your server if you're an admin!
That's all folks!





