-
 chevron_right
chevron_right
Biggest DDoSes of all time generated by protocol 0-day in HTTP/2
news.movim.eu / ArsTechnica · Friday, 13 October, 2023 - 12:50 · 1 minute

Enlarge (credit: Aurich Lawson / Getty)
In August and September, threat actors unleashed the biggest distributed denial-of-service attacks in Internet history by exploiting a previously unknown vulnerability in a key technical protocol. Unlike other high-severity zerodays in recent years— Heartbleed or log4j , for example—which caused chaos from a torrent of indiscriminate exploits, the more recent attacks, dubbed HTTP/2 Rapid Reset, were barely noticeable to all but a select few engineers.
HTTP2/Rapid Reset is a novel technique for waging DDoS, or distributed denial-of-service attacks, of an unprecedented magnitude. It wasn’t discovered until after it was already being exploited to deliver record-breaking DDoSes. One attack on a customer using the Cloudflare content delivery network peaked at 201 million requests per second, almost triple the previous record Cloudflare had seen of 71 million rps . An attack on a site using Google’s cloud infrastructure topped out at 398 million rps, more than 7.5 times bigger than the previous record Google recorded of 46 million rps.
Doing more with less
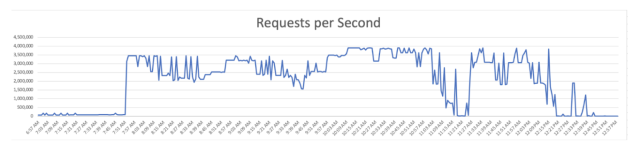
The DDoSes hitting Cloudflare came from a network of roughly 20,000 malicious machines, a relatively small number compared with many so-called botnets. The attack was all the more impressive because, unlike many DDoSes directed at Cloudflare customers, this one resulted in intermittent 4xx and 5xx errors when legitimate users attempted to connect to some websites.