-
 chevron_right
chevron_right
The W Pattern Forex Trading Guide For Beginner
Alla Traders · Wednesday, 28 December, 2022 - 15:46 edit · 1 minute
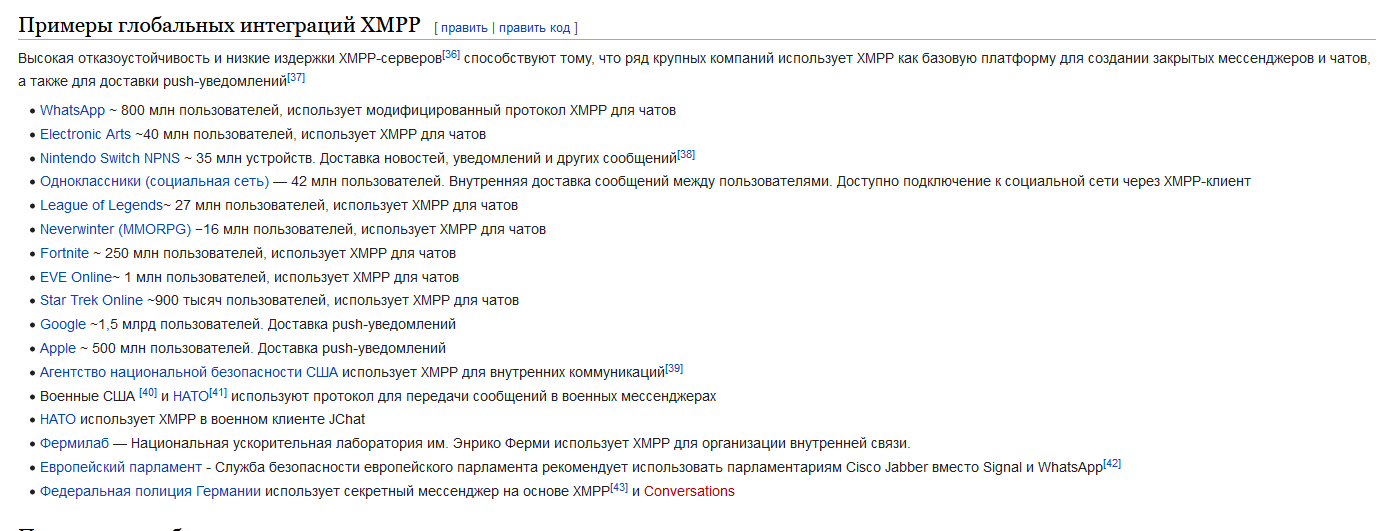
The double bottom or W pattern is the most prevalent chart pattern used in trading. In fact, this pattern is so common that it may be taken as irrefutable evidence by itself that price action is not as totally random as many say. The double bottom pattern is one of the very few that perfectly depicts the market’s direction changing. At the bottom of a downtrend, the double bottom forms itself, offering potential long entries for buyers.
What Is A Double Bottom (W Pattern)?
The double bottom pattern is a technical pattern that can be used to identify a likely reversal in the Forex market. The double bottom emerges after an extended move down and can be utilized to discover purchasing opportunities on the way up. Because of the two-touched low and the change in trend direction from downtrend to uptrend, the pattern resembles the letter “W.”
see the complete blog here Alla Traders
#forex #stock #crypto #trading #trader #features #thinkpad #postgresql #fediverse #database #apps #zimbabwe #gaming #profanity #xmpp #pipcu #sdr #wow #discussion #chirurgie #tools #ev #rf #instantmessaging #comics #alternativesto #ubuntu #lu #howto #apple #hololive #députés #ecology #chocolat #ft8 #piquetsyndical #8chan #siri #écologie #endurance #how #discord #platforms #dior #rcs #squat #1 #hydroxychloroquine #election #gif #laptops #omemo #hacking #fedora #ethot #compression #potpourri #kaamelott #meme #jitsi #freebsd #feminisme #gajim #animals #sendgnomemoney #métaverse #wordle #fastned #autopilot #cinéma #evolution #ukraine #jabber #sponsor #dessin #rando #africa #entraineur #google #zooarchaeology #community #technology #reddit #movim #ajax #calendar #moderation #snapchat #formation #review #quake #im #attentat #policy #advertising #prosody #abstention #azure #webserver #france #camping #amazon #openwebrx #maps #sncf #lci #darktable #littérature #keyboards #rendement #twitch #eu #projecteur #vieprivée #jpg #dinosaures #hardware #drawing #tyrannosaure #jappix #tgv #pcb #patents #médaille #poezio #animation