Argentina, Australia, Austria, Belgium and Brazil; just two letters of the alphabet and that’s already five countries that have implemented ISP blocking against The Pirate Bay.
Argentina, Australia, Austria, Belgium and Brazil; just two letters of the alphabet and that’s already five countries that have implemented ISP blocking against The Pirate Bay.
The growing list, which continues with Denmark and persists through Finland, France and Germany, doesn’t stop until it reaches the United Arab Emirates and finally, the UK.
That’s around 30 countries overall, give or take, that have resorted to ISP blocking because no matter what’s thrown at it, The Pirate Bay simply refuses to die.
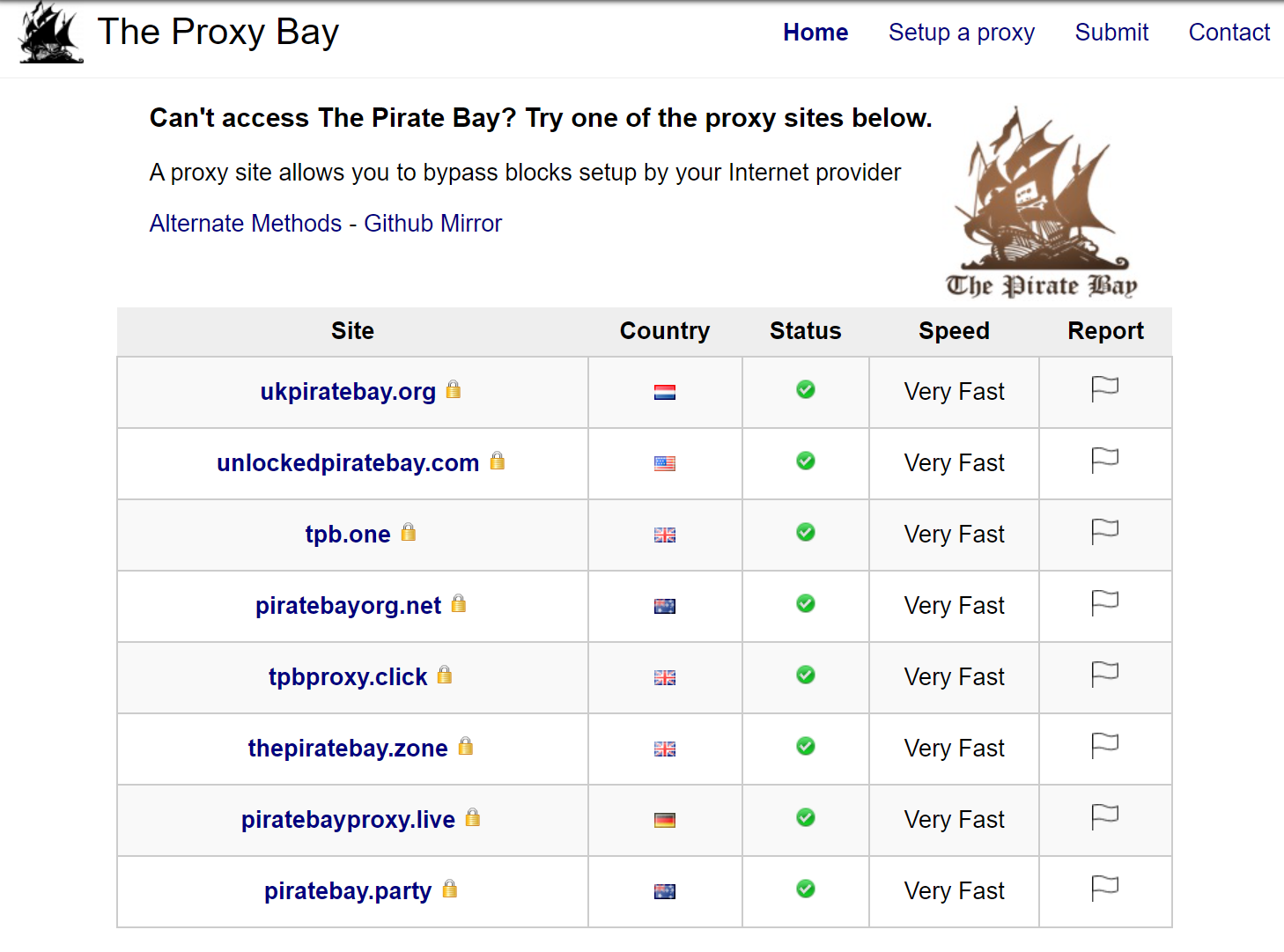
At least in part, the site is still alive after more than a decade of widespread blocking due to the existence of proxy sites. These sites tend to look and feel like The Pirate Bay but operate from different domain names that aren’t yet on ISP blocklists.
This means that otherwise blocked internet users get to enjoy broadly the same Pirate Bay experience as they did before. At least for a while.
Rightsholders Also Block Pirate Bay Proxies
As
reported
yesterday, one of the most popular Pirate Bay proxy indexing sites recently disappeared from GitHub.
ProxyBay was a significant player, one that had helped dozens of millions of users gain access to The Pirate Bay by directing them to active Pirate Bay proxy sites. However, in common with The Pirate Bay itself, proxy sites are also subjected to ISP blocking, which can render some of them redundant, not to mention inaccessible.
Given that proxy sites and proxy indexes contribute to the overall health of the Pirate Bay ‘hydra’, that got us thinking: Is the hydra alive and well? Or has it lost a few too many heads over the years?
Data Sources Used
While we’re aware that proxy sites face blocking in several countries, until today we’d never drilled into the details. It quickly became apparent that a complete overview would require significant time and resources but our short report today should help set the tone.
To weigh rightsholders’ responses to strictly Pirate Bay proxy sites, we obtained domain blocking lists used by ISPs in the UK, Denmark and Italy. The original plan was to include Portugal, India and a handful of other countries but the volume of data was soon overwhelming.
Instead of including those additional countries, we used data from the Infringing Website List (IWL) operated by the UK’s Police Intellectual Property Crime Unit.
Proxies Face Massive Blocking
After merging data from all four sources, we removed any duplicate proxy domains, any domains that weren’t clearly dedicated or directed at the Pirate Bay, plus any domains where their key role could not be identified due to downtime or other reasons.
The final total of Pirate Bay proxies, all of which are subjected to blocking and/or restrictions on business due to their appearance on the IWL, is 670 to 690 domains, give or take. While that remains a large number, including other countries’ blocklists would’ve inflated that number considerably.
The big question is whether all of those domains are live, in business, and helping to unblock The Pirate Bay. The simple answer to that is ‘no’. While we were able to test whether sites were active in some way, we couldn’t determine exactly what they were doing, unless we visited every last one and took a screenshot for proof.
…..So That’s What We Did
The image below is comprised of roughly 670 screenshots featuring obviously live proxies (mostly white), a lot of seemingly dead proxies (dark), and a surprising number of domains up for sale (mostly blue).
(click to enlarge)
It’s not possible to determine the exact reasons why so many proxies appear to have thrown in the towel, in some cases on multiple domains. That being said, it’s highly likely that ISP blocking played an important role in dampening enthusiasm for spending more money on yet another domain.
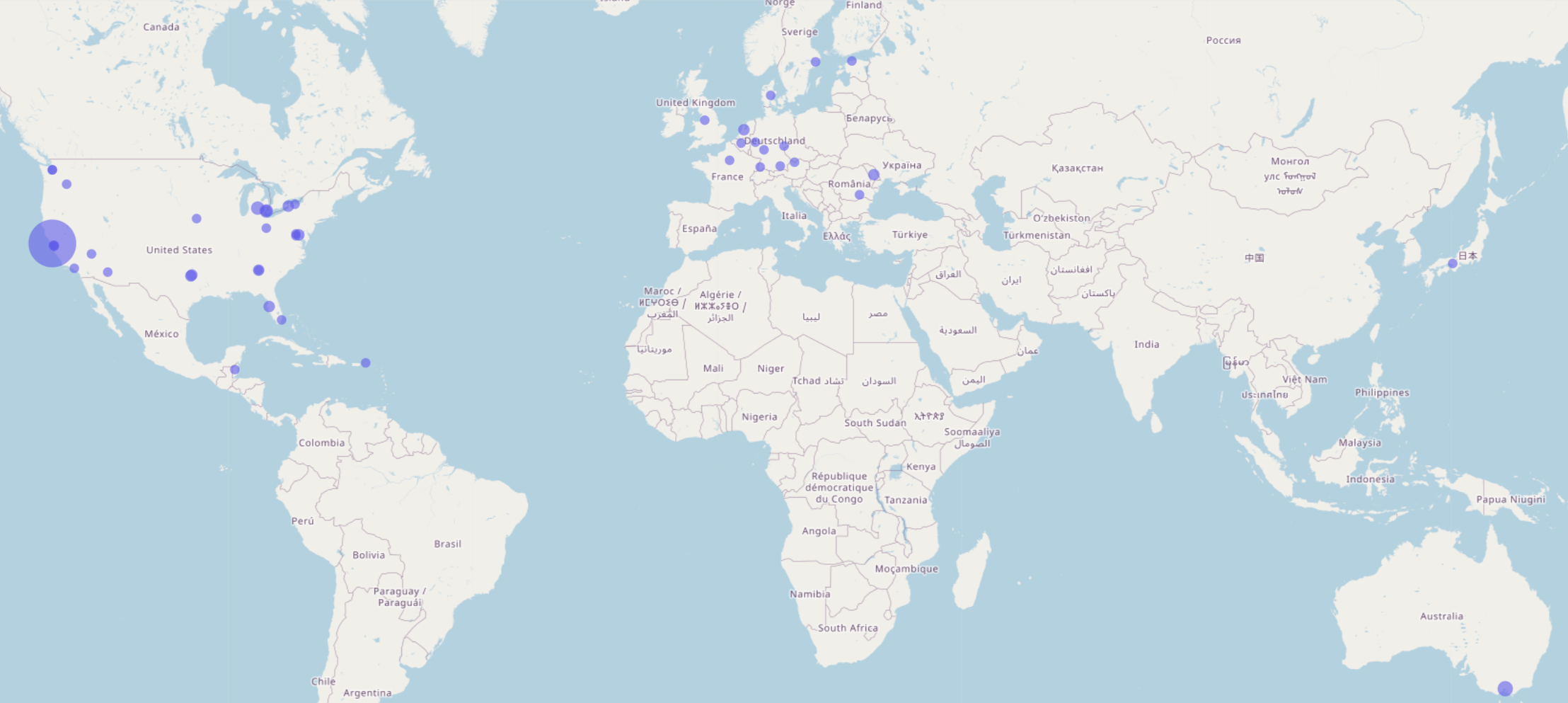
Since the data was at hand, we decided to throw all of the live domains at their DNS and then wait for a list of IP addresses to come out. We fed those into an
IP location service
which produced the map in the image below.
The large blue blob on the left, representing the location where most Pirate Bay proxies point, is the home of Cloudflare and another kind of proxy – a reverse proxy.
That means that in all likelihood, the Pirate Bay proxies are hosted somewhere else entirely, not unlike The Pirate Bay itself. At least for now.
From:
TF
, for the latest news on copyright battles, piracy and more.
 chevron_right
chevron_right