- label
-
 chevron_right
chevron_right
DuckDuckGo browser beta for Windows bakes in a lot of privacy tools
news.movim.eu / ArsTechnica · Thursday, 22 June, 2023 - 12:00
-
 chevron_right
chevron_right
Small businesses count cost of Apple’s privacy changes
news.movim.eu / ArsTechnica · Tuesday, 9 August, 2022 - 13:29
-
Sc
chevron_right
Facebook Is Now Encrypting Links to Prevent URL Stripping
news.movim.eu / Schneier · Monday, 18 July, 2022 - 14:49
-
 chevron_right
chevron_right
Facebook is receiving sensitive medical information from hospital websites
news.movim.eu / ArsTechnica · Thursday, 16 June, 2022 - 14:53
-
 chevron_right
chevron_right
Mathias Poujol-Rost ✅ · Sunday, 20 February, 2022 - 20:26
Contact publication
-
 chevron_right
chevron_right
Mathias Poujol-Rost ✅ · Thursday, 17 February, 2022 - 06:47
Contact publication
-
Co
chevron_right
StopCovid une application qui vous veut du bien ?
Auteur invité · ancapism.marevalo.net / Contrepoints · Tuesday, 28 April, 2020 - 03:15 · 10 minutes
- la pertinence de cette application repose sur un fort taux d’utilisation (minimum 60 %) qui ne peut être atteint de manière volontaire.
- des incertitudes subsistent sur le traitement des données.
- le solutionnisme technologique n’est pas une solution. L’application SAIP développée pour prévenir en cas de risques a été abandonnée peu de temps après son lancement.
- personne à ce jour n’est capable de prouver qu’une application de contact tracking fonctionne, bien au contraire.
- le téléchargement d’une application et l’activation de la fonctionnalité Bluetooth ne sont pas maîtrisés par une partie des publics les plus éloignés du numérique.
- les publics les plus éloignés du numérique n’ont pas les moyens de donner un consentement réellement libre et éclairé.
- Article paru originellement sur http://mediateurnumerique.org/ , sous licence Creative Commons By . ↩
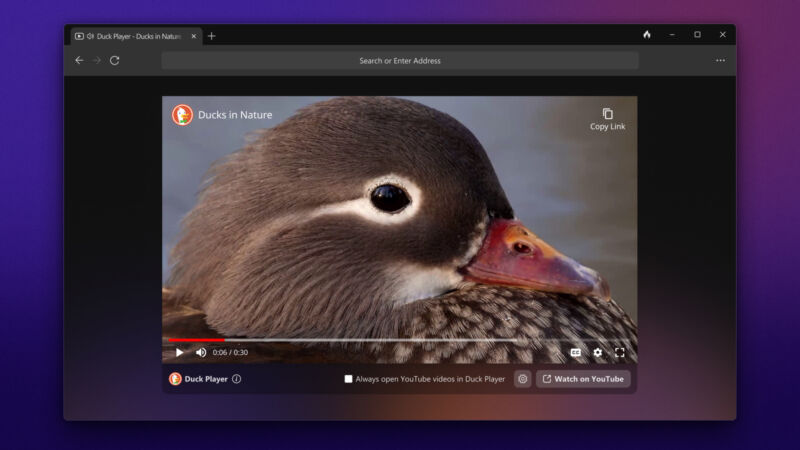
Enlarge / By using DuckDuckGo's built-in Duck Player, you should be able to avoid both advertisements and having your YouTube recommendations be affected by memes and movie clips for when you forget to open a private window. (credit: DuckDuckGo)
Privacy-focused firm DuckDuckGo has released a public beta of its browser for Windows , offering more default privacy protections and an assortment of Duck-made browsing tools.
More than a year after debuting its browser for Mac in private beta, the search engine and tracking antagonist offers many of those same features to a much wider audience. Like its Mac browser, DuckDuckGo (DDG) uses "the underlying operating system rendering API" rather than its own forked browser code. That's "a Windows WebView2 call that utilizes the Blink rendering engine underneath," according to DuckDuckGo's blog post . Fittingly, the browser reports itself as Microsoft Edge at most header-scanning sites.
Inside the DuckDuckGo browser, you'll find:

Enlarge (credit: Kentaroo Tryman | Getty Images )
Small businesses are cutting back marketing spending due to Apple’s sweeping privacy changes that have made it harder to target new customers online, in a growing trend that has led to billions of dollars in lost revenues for platforms like Facebook.
Apple last year began forcing app developers to get permission to track users and serve them personalized adverts on iPhones and iPads in changes that have transformed the online advertising sector.
Many small companies which are reliant on online ads to attract new customers told the Financial Times they did not initially notice the full impact of Apple’s restrictions until recent months, when price inflation squeezed consumer demand in major markets worldwide.
Some sites, including Facebook, add parameters to the web address for tracking purposes. These parameters have no functionality that is relevant to the user, but sites rely on them to track users across pages and properties.
Mozilla introduced support for URL stripping in Firefox 102 , which it launched in June 2022. Firefox removes tracking parameters from web addresses automatically, but only in private browsing mode or when the browser’s Tracking Protection feature is set to strict. Firefox users may enable URL stripping in all Firefox modes , but this requires manual configuration. Brave Browser strips known tracking parameters from web addresses as well.
Facebook has responded by encrypting the entire URL into a single ciphertext blob.
Since it is no longer possible to identify the tracking part of the web address, it is no longer possible to remove it from the address automatically. In other words: Facebook has the upper hand in regards to URL-based tracking at the time, and there is little that can be done about it short of finding a way to decrypt the information.

Enlarge (credit: Aurich Lawson | Getty Images)
A tracking tool installed on many hospitals’ websites has been collecting patients’ sensitive health information—including details about their medical conditions, prescriptions, and doctor’s appointments—and sending it to Facebook.
The Markup tested the websites of Newsweek’s top 100 hospitals in America. On 33 of them we found the tracker, called the Meta Pixel, sending Facebook a packet of data whenever a person clicked a button to schedule a doctor’s appointment. The data is connected to an IP address—an identifier that’s like a computer’s mailing address and can generally be linked to a specific individual or household—creating an intimate receipt of the appointment request for Facebook.


Par Loïc Gervais.
Un article de Framablog 1
Dans son adresse aux Français du 13 avril, le Président de la République Emmanuel Macron a fait mention de l’application StopCovid sans la nommer.
Plusieurs innovations font l’objet de travaux avec certains de nos partenaires européens, comme une application numérique dédiée qui, sur la base du volontariat et de l’anonymat, permettra de savoir si, oui ou non, on s’est trouvé en contact avec une personne contaminée. Vous en avez sûrement entendu parler.
Une chose est certaine, nous entendons beaucoup parler de cette application. Mais qu’en savons-nous vraiment ? Le rôle du médiateur numérique est d’accompagner le citoyen dans les enjeux liés au numérique. Autrement dit de lui donner les éléments essentiels de culture numérique pour qu’il puisse se forger une opinion sur cette application et ainsi participer au débat.
Voyons donc à travers ce billet son principe de fonctionnement dans un premier temps. Vous avez été nombreux à me questionner aussi sur les risques de sécurité informatique ainsi que sur les risques liés à nos données personnelles.
Le laboratoire de Mr Q
Dans les films de James Bond, le Professeur Q est celui qui fournit à 007 les innovations technologiques pour accomplir au mieux sa mission. Pour autant la réussite du plus célèbre des agents secrets ne repose que très partiellement sur son recours à l’aide technologique. À tel point que les inventions du Professeur Q sont pour nous autres de simples gadgets.
Quel que soit le problème, il y aura toujours une main qui se lèvera pour proposer une solution technologique. En fait, plusieurs mains se lèveront. Et dans la plupart des cas, les solutions proposées ne fonctionneront pas comme espéré. Les inventeurs réclameront davantage de crédit ou une meilleure implication du public cible.
Rarement le principe du recours à la technologie sera remis en cause en tant que tel. C’est pourtant la première question à laquelle nous devons répondre.
Avons-nous besoin de nouveaux outils technologiques pour gérer la situation actuelle ? Qu’est-ce que le corps médical attend comme fonctionnalités de ces nouveaux outils ?
En la matière dans son communiqué daté du 2 avril le Conseil Scientifique préconisait « de nouveaux outils numériques permettant de renforcer l’efficacité du contrôle sanitaire de l’épidémie »
Principe de fonctionnement
Le gouvernement s’est donc lancé dans le développement de l’application StopCovid. Le but de cette application est de limiter les contaminations en identifiant des chaînes de transmission. Il est important d’insister sur ce point.
Le but de StopCovid est de limiter la propagation du virus. L’application n’a pas pour objectif de soigner ou d’éradiquer le Coronavirus, uniquement de limiter sa propagation.
Je télécharge l’application (si je le souhaite) et si j’entre en contact avec une personne (qui possède l’application) et qui a développé le virus alors je reçois une notification. En aucun cas cela signifie que je suis moi-même contaminé. Cela m’invite à passer un test, si j’ai croisé quelqu’un positif il y a quelques jours.
Autrement dit l’application repose sur le principe que chacun joue le jeu. En effet 70 % des Français possèdent un smartphone (62 % des 60-69 ans et 44 % des 70 ans et plus). Selon une étude de l’université britannique d’Oxford publiée dans la revue « Science », un tel dispositif prouverait son efficacité si au moins 60 à 70 % de la population l’utilise.
Sachant que seuls 70 % de la population ont un smartphone, cela veut dire que dans le meilleur des cas, avec 100 % de participation et 100 % de respect de la quarantaine, il ne suffira que de confiner 25 % des cas symptomatiques.
Rand Hindi, Twitter (@randhindi) 9 avril 2020
Des questions restent en suspens. Si je suis positif est-ce que c’est moi qui le notifie à mon application ? Et si je suis notifié, comment garantir que je vais bien aller faire mon test de dépistage ? L’application repose sur une grand part de civisme des utilisateurs. Et bien sûr il faut que la technologie utilisée soit en elle-même fiable.
Sécurité
En amont de la rédaction de ce billet les questions ont tourné sur le degré de précision de l’application, la sécurité et la confidentialité. Reprenons ces questions. « Le bluetooth est il aussi précis que le GPS ? » me demande Matthieu.
A priori le choix du gouvernement s’oriente vers une technologie Bluetooth. Celle-ci a le mérite de fonctionner dans plus d’endroits (par exemple dans le métro). Le Bluetooth a un degré de précision de l’ordre de 10 mètres et est plus respectueux de ma vie privée.
Le Bluetooth localise mon téléphone, mais pas son propriétaire. Ainsi, si j’ai été en contact avec quelqu’un de positif, je recevrais une notification sans que personne puisse identifier la source.
De la même manière personne ne saura que j’ai reçu cette notification, mais juste que les appareils ont été en contact. Ces appareils seront identifiés par des références anonymes qui changeront toutes les X minutes. À 15 heures mon téléphone s’appellera YT59 à 15 heures X minutes il s’appellera RD26. Je recommande de prendre 10 minutes pour écouter mon camarade Matti Schneider à ce sujet.
Le Bluetooth ravive de mauvais souvenirs chez certains. Julien me demande ainsi si le fait d’activer le BlueTooth en permanence ne constitue pas un risque en matière de vol de données du téléphone.
Il est vrai que dans son guide du nomadisme numérique , l’Agence Nationale de la Sécurité des Systèmes d’Information « recommande de désactiver les services qui sont potentiellement sources de menaces, comme le Bluetooth » . J’ai interrogé l’ANSSI à ce sujet. Je n’ai pas eu de retour à ce jour.
Liberté
Cette application respecte toutes nos lois et toutes nos valeurs en termes de libertés publiques et de protection de la vie privée. Il n’y a aucune donnée qui est accessible, ni pour l’État, ni pour qui que ce soit.
Cédric Ô, France Info 17 avril 2020.
Marie-Laure DENIS, Présidente de la Commission Nationale Informatique et Libertés a été auditionnée par la commission des lois de l’Assemblée nationale le 8 avril 2020 a précisé les choses en la matière de son point de vue :
« Si un suivi individualisé des personnes était mis en œuvre, il faudrait d’abord, à droit constant, qu’il soit basé sur le volontariat, avec un consentement réellement libre et éclairé – et le fait de refuser l’application n’aurait aucune conséquence préjudiciable. Ensuite, la CNIL veillerait notamment à ce que ce dispositif soit mis en place pour une durée limitée. » ( Source )
En tout état de cause, la solution retenue ne peut constituer que l’un des éléments d’une réponse sanitaire plus globale. D’un point de vue technologique, l’application peut très bien être dans les clous.
C’est sur le terrain social que nos libertés pourraient être mises à rude épreuve. Pour que l’application soit efficace, il faut un grand nombre d’utilisateurs. Il faut s’attendre donc à de grandes campagnes de communication du gouvernement en ce sens.
Vos collègues de boulot vous demanderont si vous l’avez téléchargé. On ne peut pas exclure non plus que l’employeur l’installe par défaut sur les téléphones professionnels.
Le risque est que l’on s’habitue à ce type de solutions et qu’on en redemande sans même savoir si c’est efficace. En la matière, les caméras de vidéo-protection (ou vidéo-surveillance) constituent un exemple. Malgré leur coût faramineux et leur impact limité nous nous sommes habitués à être filmés partout. Tant et si bien que nous en demandons davantage, en dépit de toute objectivité ( voir par ailleurs ).
L’indispensable médiation
Le secrétaire d’État au Numérique a saisi le Conseil National du Numérique sur StopCovid. Dans sa lettre adressée à la Présidente du CNNUM, Salwa TOKO, Cédric O demande des « recommandations sur les conditions qui pourraient permettre l’adoption [de StopCovid] par le plus grand nombre et notamment sur la question essentielle de l’inclusion » .
Le ministre invite le Conseil National du Numérique à rencontrer les acteurs de la société civile. Aussi, je prends les devants et expose le point de vue d’un médiateur numérique.
Il y a quelques années, je participais avec les membres d’alors à la rédaction du rapport inclusion numérique de votre institution. Je me permets de reformuler ici la deuxième des sept propositions : « faire de la littératie pour tous le socle d’une société inclusive » .
Je participe actuellement à la plateforme Solidarité-Numérique. Nous avons reçu des milliers d’appels. Cette semaine nous devrions traiter beaucoup de demandes liées aux déclarations d’impôts. Je doute très sincèrement que nos appelants soient en mesure de donner un consentement réellement libre et éclairé concernant StopCovid .
L’une des actions qui pourrait permettre l’adoption de StopCovid est de développer davantage les actions de littératie numérique. La crise que nous traversons montre à quel point nous sommes tous collectivement en déficit numérique. On parle souvent de 13 millions de Français éloignés du numérique. Cette crise nous montre que ce chiffre est sous-évalué, largement.
Nous n’aurons pas les moyens dans les semaines qui suivent de faire monter en compétence autant de personnes. Nous n’aurons pas les moyens de donner à chaque citoyen les éléments de littératie numérique pour comprendre les tenants et les aboutissants de cette application. Je ne suis pas certain d’ailleurs que beaucoup de médiateurs numériques aient eux-mêmes ces éléments.
Pour une société numérique inclusive
Cette crise extraordinaire questionne de fond en comble nos rapports au numérique. Elle met en relief le besoin indispensable de médiation pour permettre au citoyen de prendre part au débat. Beaucoup d’informaticiens, de juristes, d’élus ont exprimé leur réserve, voire leur opposition à ce projet. Beaucoup de citoyens vont se retourner vers un médiateur numérique pour avoir un avis sur cette application.
À titre personnel, je ne peux conseiller à quiconque d’avoir recours à cette application tant qu’elle n’apporte aucune garantie suffisante. Pour autant les questions abordées à travers ce projet nous interrogent sur notre vision du vivre ensemble d’une part et sur l’impérieuse nécessité d’accompagnement aux usages numériques d’autre part. Comme je l’ai indiqué dans un précédent article , de nouveaux équilibres sont à trouver pour la médiation numérique.
—







