-
chevron_right
Weak IP Address Evidence Collapses ‘Non-Responsive Movie Pirates’ Lawsuit
news.movim.eu / TorrentFreak · Monday, 2 October, 2023 - 07:02 · 5 minutes
 Voltage Holdings is one of many mostly American movie companies that have attempted to turn piracy into profit over the last 15 years. A lawsuit the company filed in Canada is broadly the same as others filed elsewhere but the same cannot be said about the outcome.
Voltage Holdings is one of many mostly American movie companies that have attempted to turn piracy into profit over the last 15 years. A lawsuit the company filed in Canada is broadly the same as others filed elsewhere but the same cannot be said about the outcome.
Background
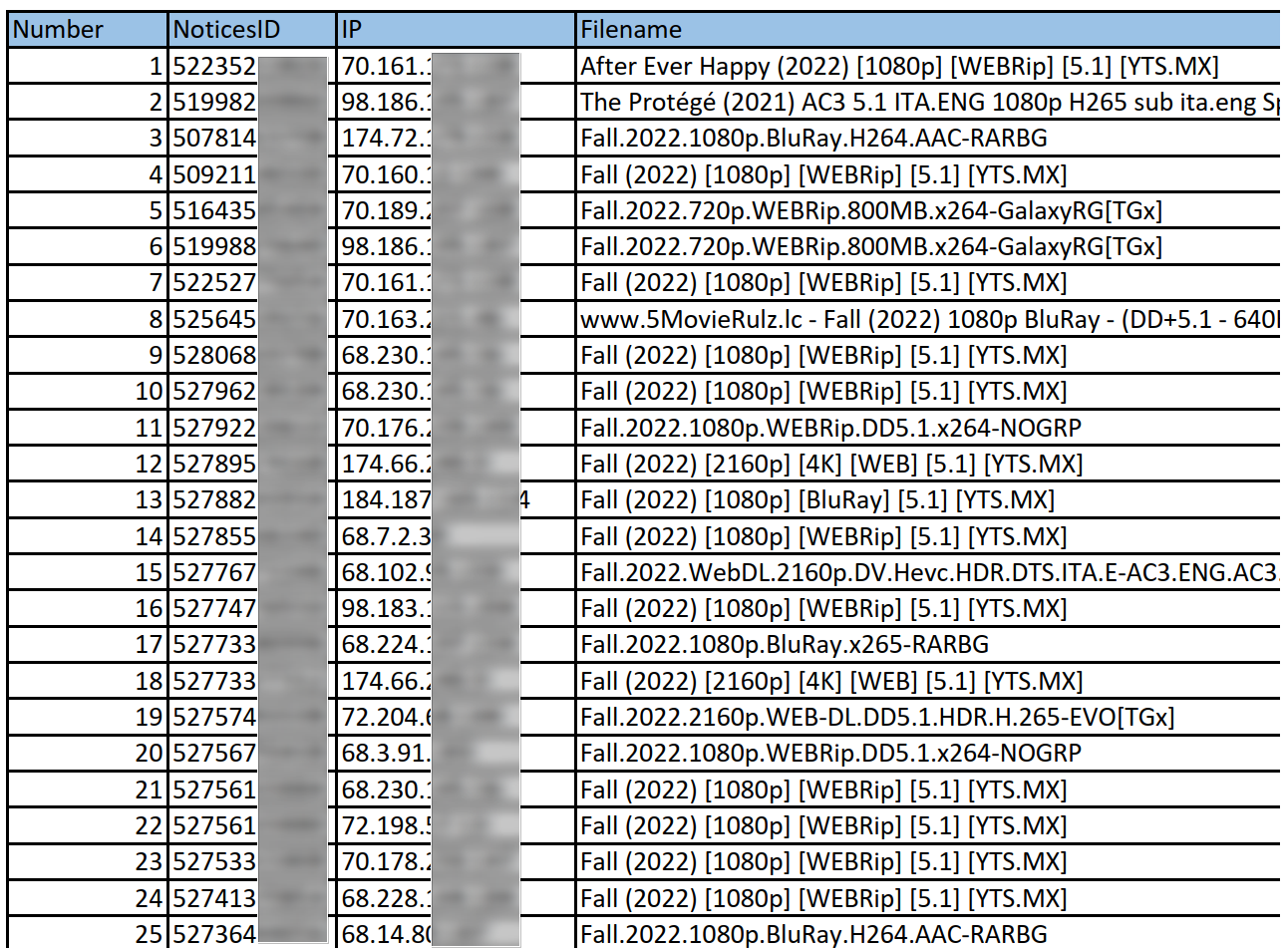
In 2017, piracy monitoring company Maverickeye collected IP addresses of BitTorrent users sharing the Voltage-owned sci-fi movie ‘Revolt’. Canada operates a so-called ‘notice-and-notice’ regime so Voltage identified the ISPs related to the IP addresses and warning notices were sent to the relevant subscribers. Second notices were sent after Maverickeye found the same IP addresses sharing the same work a week or more later.
In March 2018, Voltage filed a statement of claim against 110 ‘Doe’ defendants, identified only by their IP addresses. Voltage later obtained a so-called Norwich order which compelled the ISPs to disclose the names and addresses of the subscribers.
Voltage labeled a subset of those subscribers “the worst of the worst” and since they failed to respond, the company requested default judgment at Canada’s Federal Court.
Justice Angela Furlanetto agreed the defendants were in default but since Voltage only presented IP address-based evidence, questions remained over who had actually shared the movie.
The Judge said that there wasn’t enough evidence to show a direct link to the subscriber or draw an adverse inference. Voltage argued that if the subscriber wasn’t the infringer, the fact that they had already received warnings under Canada’s ‘notice-and-notice’ regime, among other things, meant that they should be held liable for ‘authorizing’ infringement carried out by others.
In June 2022, Justice Furlanetto declined default judgment but also refused to dismiss the case. Voltage was given more time to present evidence to support direct infringement or authorization but the company took its case to the Federal Court of Appeal instead.
Basis for Voltage’s Appeal
In its 36-page memorandum filed in November 2022, Voltage outlined two legal theories; either the billpayers pirated the movie themselves (direct infringement), or they authorized someone else’s direct infringement by allowing them to continue pirating Voltage’s movie, despite receiving warning notices from their ISPs.
Arguments were heard on March 28, 2023, and three appeal court judges (Justices Donald J. Rennie, David W. Stratas, Wyman W. Webb) handed down their judgment last week.
The judgment says that the appeal engages two issues: the jurisprudence on what constitutes direct infringement and authorizing infringement, and the burden of proof and circumstances under which an adverse inference can be drawn.
“These issues are closely interrelated. The jurisprudence with respect to the law of copyright determines the minimum evidentiary requirements to establish the asserted types of infringement; in other words, the jurisprudence constrains the extent to which an adverse inference may be drawn in the context of online copyright infringement,” the judgment reads.
Judgment Guided By Supreme Court Ruling in 2022
According to Voltage, once it had presented all “technologically available” evidence to the Court, a “tactical burden of proof” shifted to the internet subscribers. This effectively meant they had to show they were not the infringers. In respect of its authorization claims, Voltage said that Justice Furlanetto was wrong to insist on more evidence; the fact that the subscribers received notices yet failed to control their internet connections was sufficient.
The judgment deals with the authorization claims first, guided by a Supreme Court decision handed down in 2022 in Society of Composers, Authors and Music Publishers of Canada v. Entertainment Software Association .
“The Supreme Court endorsed the Copyright Board’s determination that ‘it is the act of posting [the work] that constitutes authorization’ because the person who makes the work available ‘either controls or purports to control the right to communicate it’ and ‘invites anyone with Internet access to have the work communicated to them. The authorizer is the individual directly engaging with the copyrighted material,” the judgment clarifies.
As a result, the Court of Appeal says that whoever used the subscribers’ internet connections to make Voltage’s movie available for download, authorized the infringement. The Supreme Court found that an authorizer permits reproduction but Voltage claims that an authorizer is someone who permits someone to permit reproduction.
The difference in opinion would prove fatal.
Collisions in Copyright Law
Justice Rennie says the Voltage appeal fails to show “any reversible error” in the Federal Court’s decision. Furthermore, Voltage’s arguments on authorization are “inconsistent” with the Supreme Court’s 2022 decision. Voltage’s claims of direct infringement also run into trouble.
“Although it accepted that individuals using each respondents’ IP address had infringed the appellant’s copyright by uploading the Work, the Federal Court found that it could not conclude at this time that the respondents were themselves those particular
individuals. I agree,” Justice Rennie writes.
On the question of a subscriber’s failure to defend, the Judge agrees that can lead to an adverse inference. However, just because a defendant is found to be in default at an early stage, it does not necessarily follow that an adverse inference should be drawn at the same stage.
“If the fact that a defendant was in default automatically allowed for adverse inferences at the second stage of the test for motions for default judgment, plaintiffs on ex parte motions for default judgment would need to present no evidence to the court in order to be successful. Some evidence is required,” Justice Rennie continues.
Indeed, the Federal Court held that “something more is needed than the bare assertion that a subscriber is, by default, the user responsible for infringement.” Voltage failed to provide sufficient evidence, the Court of Appeal notes, so no adverse inference could be drawn.
Court of Appeal Tightens the Noose
Voltage’s reliance on infringement warnings to show subscribers’ failure to exercise control – over internet connections and connected devices – fails.
As clarified in the Supreme Court decision, authorization depends on the alleged authorizer’s control over the person who committed the resulting infringement; it does not depend on the alleged authorizer’s control over the supply of their technology.
Furthermore, to establish an infringing activity, there must be evidence to show what the activity does to the work in question.
“Posting a work online and inviting others to view it engages the author’s authorization right; however, sharing internet access after receiving notices of alleged infringement does nothing to the work in question, and does not therefore engage any copyright interest granted to the author exclusively,” the Court of Appeal notes.
Conclusion: Voltage’s Appeal is Dismissed
From the judgment: “In the factual matrix of this case and at this relatively early stage of this case, the defendants’ lack of participation in litigation does not offset the plaintiff’s lack of evidence.
“The Federal Court was not obligated to draw an adverse inference at this stage of the litigation merely because the respondents had, by their silence, not put forward sufficient evidence to rebut the appellant’s allegations,” Justice Rennie concludes.
For these reasons, Justices Rennie, Stratas, and Webb, dismissed the appeal.
The full judgment is available here ( pdf )
From: TF , for the latest news on copyright battles, piracy and more.

 In 2003, the World Wide Web was still in its infancy. Dial-up connections were still the default and YouTube, Facebook, and Gmail had yet to be invented.
In 2003, the World Wide Web was still in its infancy. Dial-up connections were still the default and YouTube, Facebook, and Gmail had yet to be invented.




 Over the past several years, adult entertainment company Strike 3 Holdings has filed
Over the past several years, adult entertainment company Strike 3 Holdings has filed