Sky has fought piracy mechanisms of all kinds over the years. From set-top box modifications to viewing card tampering, blocking, even full PC-based emulation, the pay TV company has seen it all.
Sky has fought piracy mechanisms of all kinds over the years. From set-top box modifications to viewing card tampering, blocking, even full PC-based emulation, the pay TV company has seen it all.
Exploits that are relatively easy to pull off and work at scale are considered serious threats. Last month we reported on the sale of
Sky encryption keys
on platforms including Telegram. That type of thing has been going on for some time, but over the space of a few days, direct URLs to watch Sky content in the UK, Italy, and Germany, were posted online and inevitably began to spread.
Free Decryption Key Extractors
This week a related problem was observed by intelligence and investigations company,
Kopjra S.r.l
. Working as a Sky anti-piracy partner in Italy, Kopjra sprang into action after spotting software uploaded to GitHub by a user who only signed up this month.
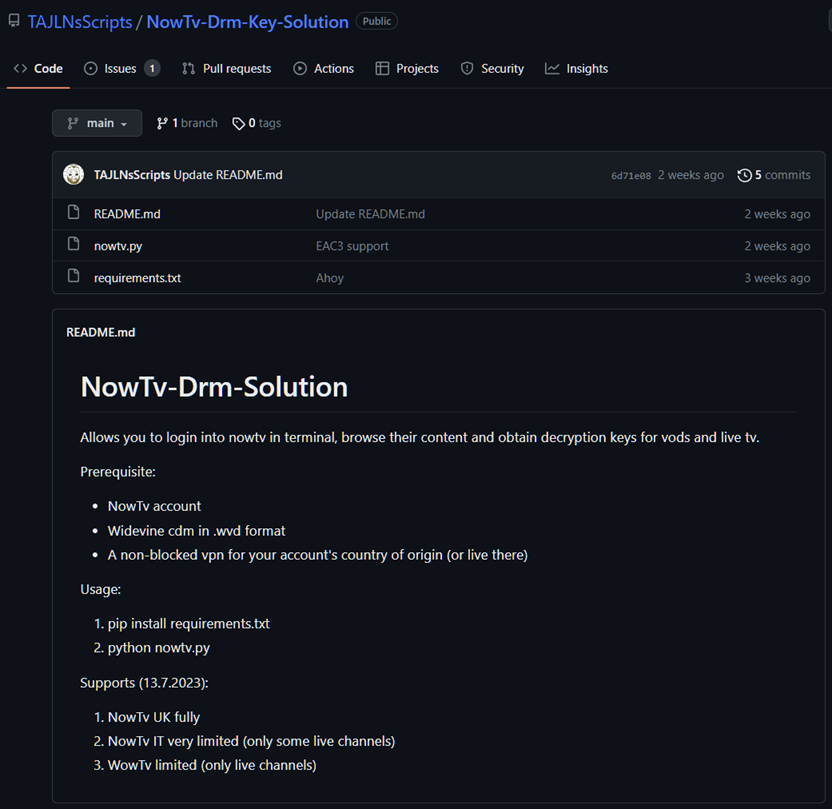
The user account ‘TAJLNsScripts’ was created in early July and currently focuses on video platform-related tools. The first script causing concern at Sky was written in Python and claims to allow users to log in to Now TV via a terminal window, browse the platform’s content, and then obtain decryption keys for both VOD content and live TV.
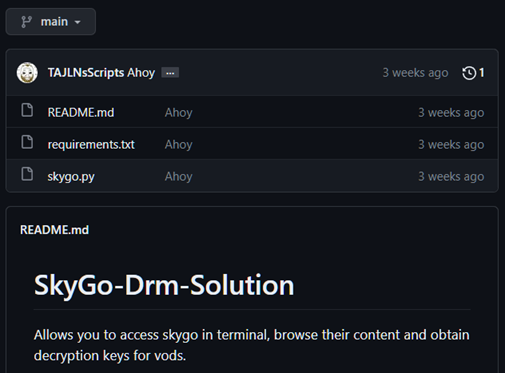
A second repository named ‘SkyGo-Drm-Solution’ offered a Python script with features broadly in line with the VOD capability of its Now TV-focused namesake. In order to function, the tool requires users to take an extra step using a specific cookie culled from Sky’s platform.
While still a concern for Sky, the extra steps and the question of what to do with the keys once obtained, are likely to put off most people from venturing further. For people with a rudimentary understanding of how these things work, nothing here is particularly difficult either.
The broad underlying concern is that these scripts and others like them exploit a fundamental weakness that a) can’t be easily fixed and b) goes way beyond Sky. It’s a fairly sensitive topic, to put it mildly.
Kopjra’s Aggressively-Worded DMCA Takedown
After identifying itself as representing Sky UK, Kopjra informed GitHub via a DMCA notice that the tools allow for the decryption of Sky content otherwise protected by Widevine DRM.
“This activity is manifestly illicit, and it represents a violation of our Client’s exclusive intellectual property rights (COPYRIGHT) on the Asset, given that our Client has never authorized – neither intends to authorize – any of the Page/s displaying contents concerning the Asset,” the notice reads.
“In consideration of the above, we formally invite you to immediately remove – within 24 hours of receipt of this letter – the above-mentioned Page/s, to disable access to users and cease any further publishing of any content concerning the Asset on the Page/s.”
As the image above shows, the scripts in question were uploaded to GitHub roughly three weeks ago. The first and second repo were both created on July 8, approximately six minutes apart. Both had obvious topic tags and were very easy to find from the beginning.
After being publicly exposed for a considerable time, removing the software was presented as an emergency matter, with Kopjra informing GitHub that anything short of immediate compliance would render the coding platform liable for losses.
“We bring to your attention that, in case of failure to comply with the above requests, you will be deemed directly responsible for the persisting infringement of our Client’s intellectual property rights as well as for the consequent damages (both economic and non-economic) suffered and that can be suffered in the future,” the notice warned.
GitHub Removes Software
The DMCA takedown notice published by GitHub shows that the developer of the software was given an opportunity to
make changes
to their code, provided with advice on how to
submit a counternotice
, and directed towards
GitHub-supplied legal resources
.
These steps are part of GitHub’s commitment to
supporting developers
following the
attempted takedown
of youtube-dl in 2021. The commitment doesn’t imply that GitHub endorses a developer’s work, but the company does believe that coders should have the
freedom to tinker
.
What response was received by GitHub, if any, isn’t detailed
in the notice
, but the end result was both repositories being disabled along with several forks. The developer’s account was not suspended due to the takedown notice, but it now contains just three repos rather than the original five.
For Sky and its anti-piracy partners, this represents just one of many takedowns filed already this month, mostly hoping to make sites and services much harder to find.
Continuous DMCA Notices
Sky has several anti-piracy partners and they are always kept busy tackling various threats. Takedown notices targeting pirate IPTV services, their sales portals in particular, are sent to Google on a regular basis. The strategy includes making numerous claims in respect of different types of infringement.
For example, notices like these (
1
,
2
) claim that infringing links to copyrighted content are provided by the sites in question, but very rarely are any links included in takedown notices. To avoid the notices being rejected, they carry
additional claims
that the sites display Sky’s logos without permission. Since that’s usually the case and is easily proven, these takedowns can be effective.
Sky isn’t simply a broadcaster, though, it owns content too. That leads to takedown
notices like this
which target sites that directly host movies and TV shows, or allow them to be streamed via their platforms.
Like many similar companies, Sky has to deal with a persistent threat from piracy apps, usually in the form of Android APK files offered on various sites. They are tackled with notices
like this
, while platforms offering DRM keys are dealt with in
broadly the same way
.
Image credit:
Pixabay
/
TheDigitalArtist
From:
TF
, for the latest news on copyright battles, piracy and more.
 chevron_right
chevron_right