-
 chevron_right
chevron_right
Mass exploitation of Ivanti VPNs is infecting networks around the globe
news.movim.eu / ArsTechnica · Wednesday, 24 January, 2024 - 01:36

Enlarge / Cybercriminals or anonymous hackers use malware on mobile phones to hack personal and business passwords online. (credit: Getty Images)
Hackers suspected of working for the Chinese government are mass exploiting a pair of critical vulnerabilities that give them complete control of virtual private network appliances sold by Ivanti, researchers said.
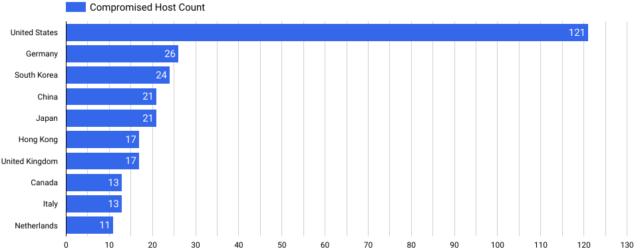
As of Tuesday morning, security company Censys detected 492 Ivanti VPNs that remained infected out of 26,000 devices exposed to the Internet. More than a quarter of the compromised VPNs—121—resided in the US. The three countries with the next biggest concentrations were Germany, with 26, South Korea, with 24, and China, with 21.
Microsoft’s customer cloud service hosted the most infected devices with 13, followed by cloud environments from Amazon with 12, and Comcast at 10.