-
chevron_right
Music Industry Puts Pressure on ‘Parasitic’ Streaming App Musi
news.movim.eu / TorrentFreak · Yesterday - 18:27 · 5 minutes
 App stores are littered with apps that promise free access to music, but only few live up to expectations.
Musi
is one of them.
App stores are littered with apps that promise free access to music, but only few live up to expectations.
Musi
is one of them.
The music app made headlines in 2016 when its founders, who were teenagers at the time, presented their brainchild in an episode of the Canadian edition of Dragons’ Den.
In essence, the software itself is relatively simple. Musi can stream music, which it sources from YouTube, and allows users to create and share playlists. It essentially uses YouTube as a music library, without showing the video.
This functionality directly rivals other streaming apps such as Spotify. However, since content is sourced from YouTube, costs associated with payments to labels are absent from the Musi equation, and that means it’s much cheaper to run.
This business model is a win-win for Musi’s operators and the platform’s users. Music industry insiders, on the other hand, are less pleased. They describe the app as “parasitic”, a reference to the app’s reliance on YouTube content, which it allegedly obtains by circumventing the platform’s technical protection measures.
For Dragon’s Den judge Joe Mimran, potential challenges to the business proved too much. While he was initially interested in investing $125,000 in exchange for a 15 percent stake in the company, the entrepreneur eventually walked away from the deal due to legal concerns.
“I was advised that when companies such as Musi get to a critical size, they could be sued for past use by the publishers,” Mimran informed the Financial Post in 2016.
Musi’s Millions
Musi didn’t throw in the towel after this setback. The app, which was already operational, continued to grow its user base in Apple’s iOS store. In the years that followed, it was downloaded dozens of millions of times.
Currently, Musi is ranked 5th in the App Store’s music category with over 3.5 million mostly positive ratings. That’s truly remarkable for a bootstrapped company that relied on YouTube, without any direct licensing deals in place with the major labels.

Earlier this year, a Wired piece highlighted Musi’s success, while also shedding some light on the legal concerns. The piece doesn’t offer any conclusions, but it suggests that the app is making many millions of dollars by operating in a ‘gray area’.
At the headquarters of global music industry body IFPI, legal matters are black or white, however. The group has had the Musi app in its crosshairs for a while. Information reviewed by TorrentFreak shows that legal pressure is building.
IFPI Reports Musi to Apple
TorrentFreak learned that IFPI reported the Musi app to the App Store last summer. Apple had already removed Musi years ago but later reinstated it. With this new request, the music group hoped for a better outcome.
Four days after IFPI submitted its complaint, U.S. legal counsel for Musi Inc. reached out to IFPI, refuting its claims. Musi’s lawyer argued that the app was merely providing access to publicly available music, stressing that it doesn’t store any content on its servers.
It’s not clear whether Apple took any position in this dispute. We do know that the company, which typically has rigorous copyright standards, didn’t remove Musi from the app store.
Apple’s inaction shows that the legalities surrounding the software are certainly not straightforward. IFPI continued to press on, however, and they eventually booked a small success, which was noticeable for Musi users too.
Secret Sauce
After the initial back and forth in July last year proved unsuccessful, IFPI reached out to Musi’s law firm again in September. Among other things, the music group specifically called out Musi’s “secret sauce” feature which, purportedly, provided access to pre-release music.
The exact contents of the letter are unknown but, in October 2023, Musi permanently removed the “secret sauce” feature.
Meanwhile, IFPI continued to hammer on the precarious legal situation it believes Musi to be in. The group has two main arguments, starting with the claim that the app circumvents YouTube’s technical protection measures.
In addition, it argues that Musi infringes its members’ rights by communicating their works through ‘new means’ to a ‘new audience’.
Musi Inc, however, continues to refute these claims though its legal team and maintains that it operates within the boundaries of copyright law.
Escalation to Apply Maximum Pressure
The communication between IFPI, Musi, and Apple continued into 2024 and the status quo remains. Apple has decided to leave the matter open for now and Musi continues to add over a million new downloads per month, frustrating IFPI.
Around February, the music group proposed to escalate the matter, encouraging its members to help out by putting pressure on Apple, while also involving YouTube in the matter. The plans are as follows, paraphrased:
– Music companies might want to complain to Apple about Musi, using their existing contacts at the company.
– In addition, they should motivate YouTube to take an active stance against the app’s developers, and complain to Apple as well.
– IFPI, for its part, should inquire among legal contacts to see whether there’s a basis for a lawsuit against Musi.
These plans would use existing business relationships to tackle the Musi problem. Whether any of these suggestions were followed up, and if so, to what extent, is unknown. The proposal is a few months old by now and from the outside there doesn’t appear to be much movement. That could easily change, of course.
After more than a year, users of the Musi app haven’t noticed anything new since much of the pressure is applied behind closed doors. In itself that’s an interesting observation, as it makes one wonder what else is going on.
It’s clear, however, that IFPI can garner the full power of its high-profile record label members. These are also the names that are likely to be listed on a lawsuit, if it ever comes to that.
From: TF , for the latest news on copyright battles, piracy and more.


 Free music is easy to find nowadays. Just head over to YouTube and there are millions of tracks, including many of the most recent releases.
Free music is easy to find nowadays. Just head over to YouTube and there are millions of tracks, including many of the most recent releases.



 Founded in 2010, Hikari-no-Akari (HnA) positioned itself as the go-to site for fans of Japanese music.
Founded in 2010, Hikari-no-Akari (HnA) positioned itself as the go-to site for fans of Japanese music.
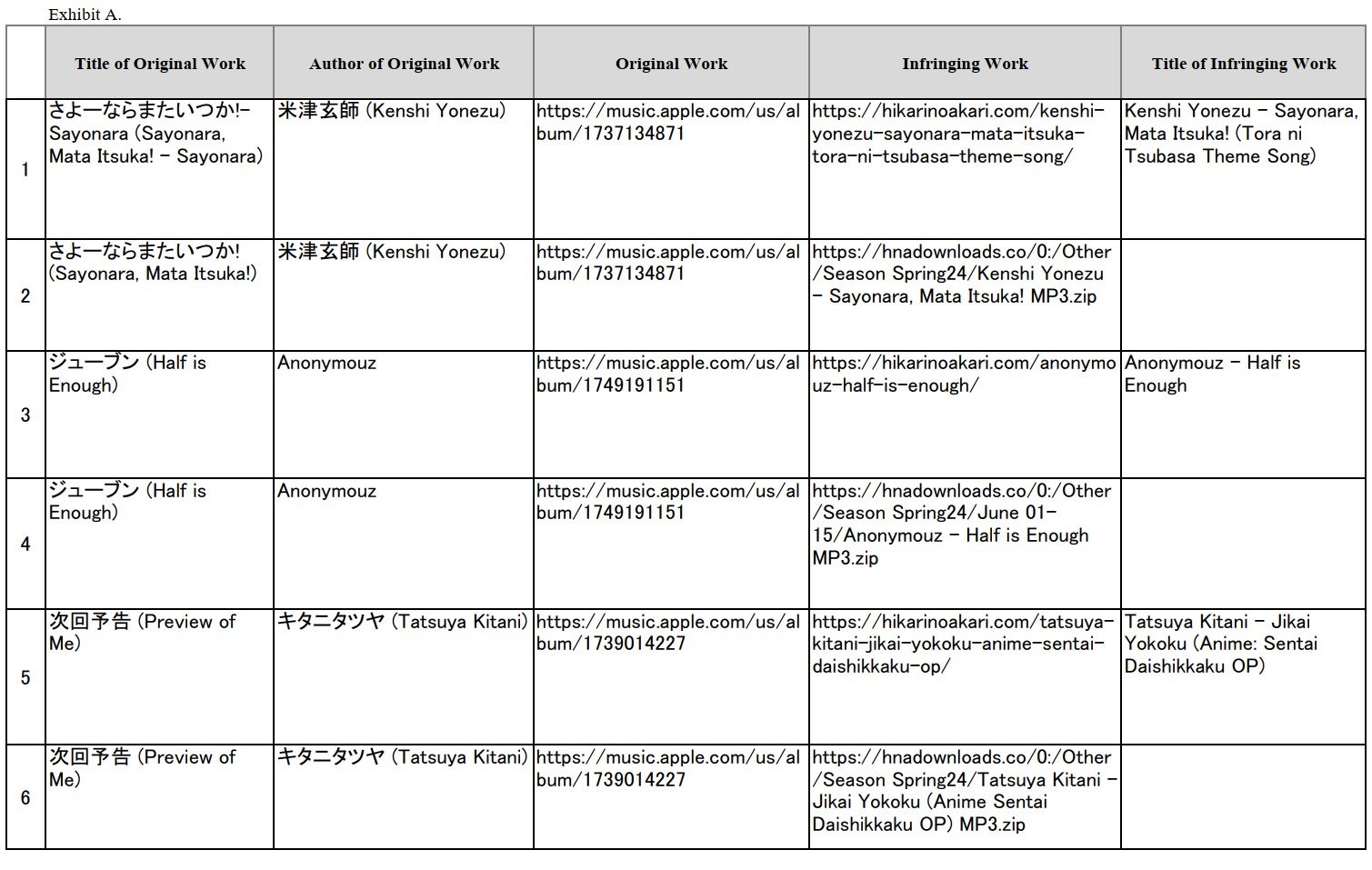
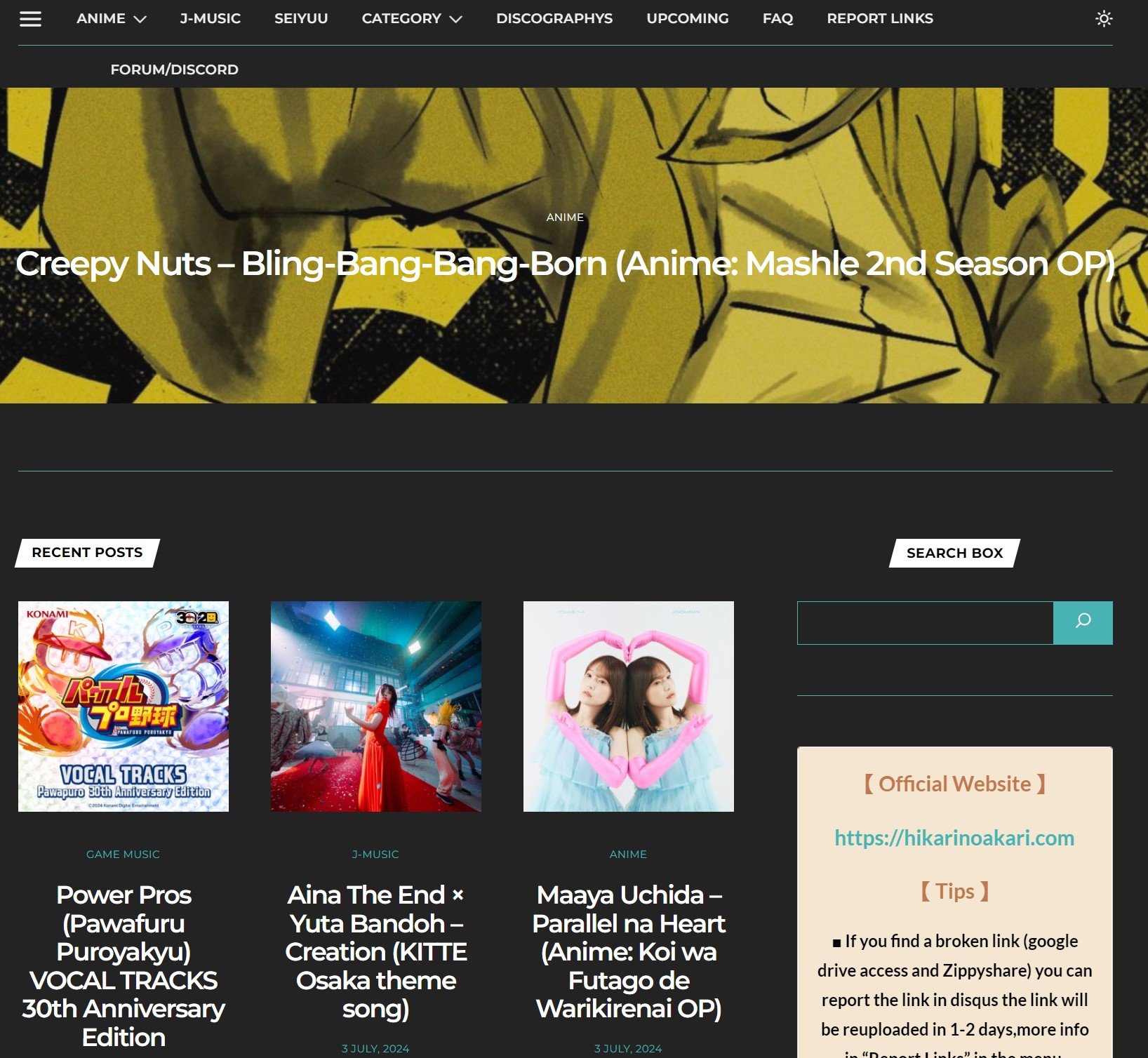

 Offering pirate streaming services is a serious offense in the UK, where several people have received multi-year prison sentences in recent history.
Offering pirate streaming services is a serious offense in the UK, where several people have received multi-year prison sentences in recent history.