-
 chevron_right
chevron_right
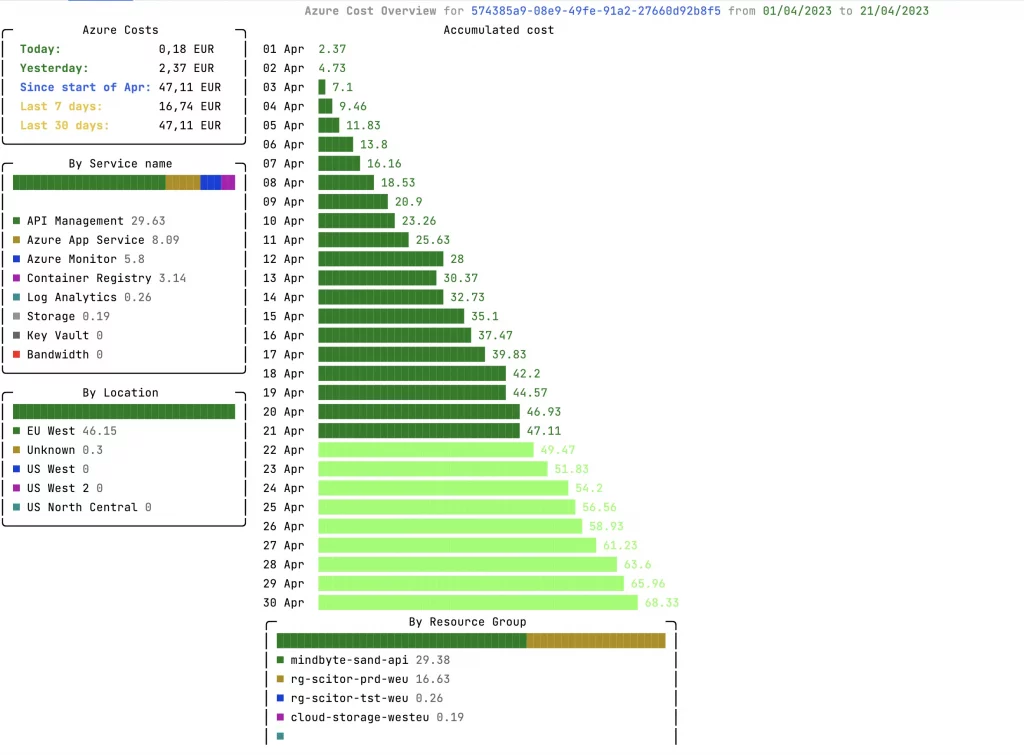
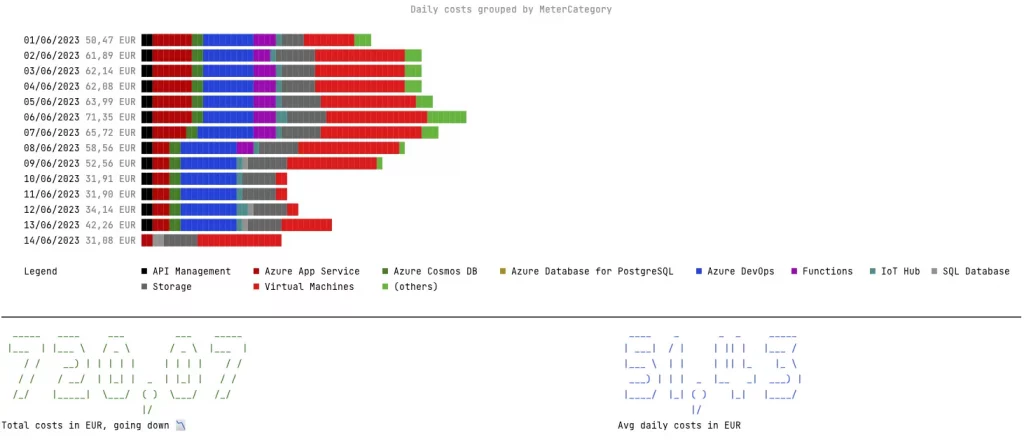
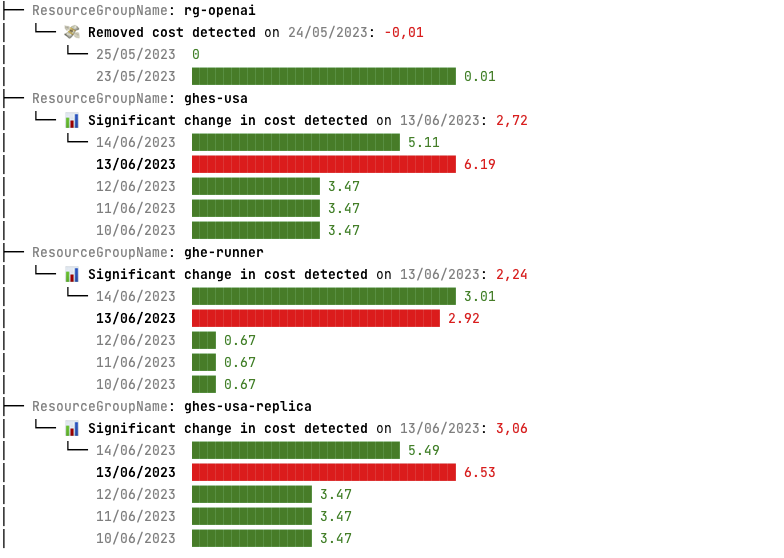
CrowdStrike fixes start at “reboot up to 15 times” and get more complex from there
news.movim.eu / ArsTechnica · Friday, 19 July - 15:43

Airlines, payment processors, 911 call centers, TV networks, and other businesses have been scrambling this morning after a buggy update to CrowdStrike's Falcon security software caused Windows-based systems to crash with a dreaded blue screen of death (BSOD) error message.
We're updating our story about the outage with new details as we have them. Microsoft and CrowdStrike both say that "the affected update has been pulled," so what's most important for IT admins in the short term is getting their systems back up and running again. According to guidance from Microsoft, fixes range from annoying but easy to incredibly time-consuming and complex, depending on the number of systems you have to fix and the way your systems are configured.
Microsoft's Azure status page outlines several fixes. The first and easiest is simply to try to reboot affected machines over and over, which gives affected machines multiple chances to try to grab CrowdStrike's non-broken update before the bad driver can cause the BSOD. Microsoft says that some of its customers have had to reboot their systems as many as 15 times to pull down the update.