-
 chevron_right
chevron_right
Ransomware attackers quickly weaponize PHP vulnerability with 9.8 severity rating
news.movim.eu / ArsTechnica · Friday, 14 June - 19:40 · 1 minute

Enlarge (credit: Getty Images)
Ransomware criminals have quickly weaponized an easy-to-exploit vulnerability in the PHP programming language that executes malicious code on web servers, security researchers said.
As of Thursday, Internet scans performed by security firm Censys had detected 1,000 servers infected by a ransomware strain known as TellYouThePass, down from 1,800 detected on Monday. The servers, primarily located in China, no longer display their usual content; instead, many list the site’s file directory, which shows all files have been given a .locked extension, indicating they have been encrypted. An accompanying ransom note demands roughly $6,500 in exchange for the decryption key.
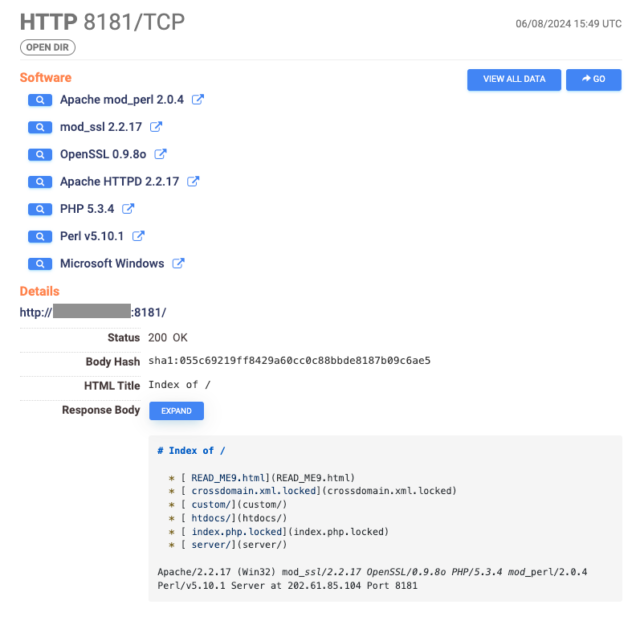
The output of PHP servers infected by TellYouThePass ransomware. (credit: Censys)

The accompanying ransom note. (credit: Censys)
When opportunity knocks
The vulnerability , tracked as CVE-2024-4577 and carrying a severity rating of 9.8 out of 10, stems from errors in the way PHP converts Unicode characters into ASCII. A feature built into Windows known as Best Fit allows attackers to use a technique known as argument injection to convert user-supplied input into characters that pass malicious commands to the main PHP application. Exploits allow attackers to bypass CVE-2012-1823, a critical code execution vulnerability patched in PHP in 2012.






